Learn how to safeguard your organization from North Korean threat actors who employ sophisticated social engineering tactics to deceive recipients. Find out how to update your DMARC policies and take necessary precautions to protect your sensitive information and communications.
Understanding North Korean Phishing Tactics
North Korean threat actors have been employing sophisticated social engineering tactics to deceive recipients and gather intelligence. The U.S. government has issued a cybersecurity advisory cautioning organizations about these tactics and the need to protect sensitive information and communications.
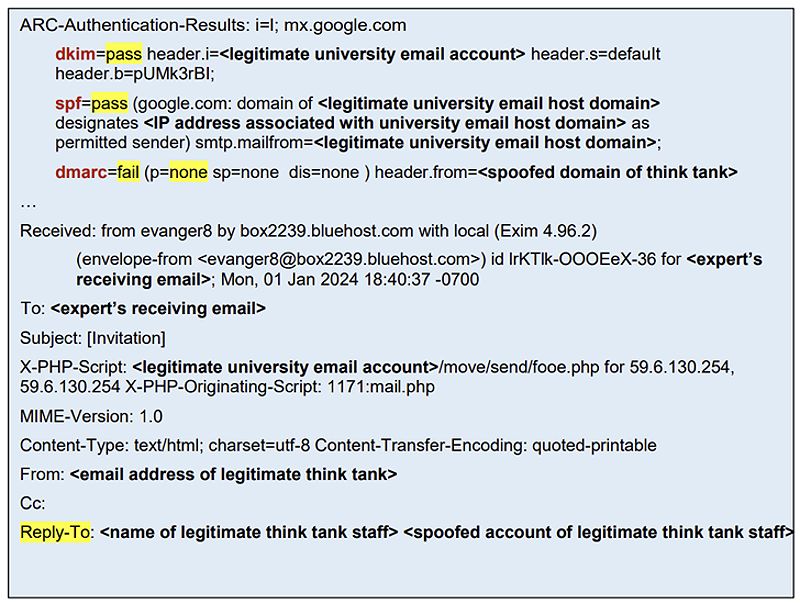
The advisory, jointly published by the National Security Agency (NSA), the Federal Bureau of Investigation (FBI), and the Department of State, highlights how North Korean threat actors, specifically the Kimsuky group, use spear-phishing campaigns to gain unauthorized access to private documents, research, and communications. They exploit improperly configured DNS Domain-based Message Authentication, Reporting, and Conformance (DMARC) record policies to send fraudulent emails that appear to originate from legitimate sources.
By impersonating subject matter experts in think tanks, academia, journalism, and independent research, the threat actors engage targets in prolonged conversations to build trust. They seek the opinions of foreign policy experts on topics such as nuclear disarmament, U.S.-South Korea policies, and sanctions. Instead of sending malware or attempting to harvest credentials directly, they rely on obtaining the targets' opinions or analysis through conversation.
The Vulnerability of Improperly Configured DMARC Policies
One key factor that enables North Korean threat actors to succeed in their phishing campaigns is the lack of properly configured DMARC policies. Many of the entities spoofed by the Kimsuky group did not have enabled or enforced DMARC policies, allowing fraudulent emails to bypass security checks and ensure delivery.
Kimsuky also leverages free email addresses that spoof the same persona in the reply-to field, further convincing the target that they are engaging with legitimate personnel. This combination of exploiting weak DMARC policies and using convincing email addresses increases the likelihood of victims falling for the phishing attempts.
Protecting Against North Korean Phishing Attacks
To mitigate the risk of falling victim to these phishing campaigns, organizations are advised to update their DMARC policies. By instructing their email servers to treat emails that fail DMARC checks as suspicious or spam, organizations can quarantine or reject such messages.
It is also recommended to set up an email address in the DMARC record to receive aggregate feedback reports. This allows organizations to monitor and analyze the effectiveness of their DMARC policies and take necessary actions to enhance their email security.
Additionally, organizations should educate their employees about the tactics employed by North Korean threat actors and the importance of being cautious when interacting with emails from unfamiliar sources. Training programs can help employees recognize phishing attempts and report suspicious emails to the appropriate IT personnel.
Conclusion
The cybersecurity advisory from the U.S. government serves as a reminder of the ongoing threat posed by North Korean threat actors. Their use of sophisticated social engineering techniques, combined with exploiting weak DMARC policies, underscores the need for organizations to remain vigilant and take necessary precautions to protect their sensitive information and communications.