Explore the rising threat of Business Email Compromise (BEC) attacks and the emergence of QR code-related frauds. Learn how fraudsters are leveraging Generative AI to craft convincing emails and how QR codes are being exploited to steal sensitive data.
The Growing Threat of Business Email Compromise
Business Email Compromise (BEC) attacks are on the rise, becoming a prominent form of cyber attack. With the help of Generative AI, fraudsters are now able to craft sophisticated emails that convincingly impersonate popular brands and businesses. This article delves into the growing threat of BEC attacks and explores the role of AI in facilitating social engineering-based frauds.
Perpetrators of BEC attacks use social engineering techniques to deceive victims into providing money and sensitive information, resulting in significant profits. Generative AI has played a crucial role in the success of these attacks by enabling fraudsters to create well-written emails that appear authentic and professional. The increasing prevalence of BEC attacks highlights the need for individuals and organizations to be vigilant and adopt robust security measures.
The Rise of QR Code Attacks
QR codes, once seen as convenient and trustworthy tools, are now being exploited by cybercriminals. A report by Perception Point reveals that 6% of QR codes received via email were found to be cyber attacks. This new form of fraud, known as quishing, poses a significant threat to individuals and businesses alike.
Quishing involves enticing victims to scan malicious QR codes, granting attackers access to sensitive data that can be exploited for nefarious purposes. The ease and ubiquity of QR code scanning make this type of attack particularly concerning. It is crucial for individuals to exercise caution when scanning QR codes and for businesses to implement strong security measures to protect against this emerging threat.
The Growing Threat of Business Email Compromise
Business Email Compromise (BEC) attacks are on the rise, becoming a prominent form of cyber attack. With the help of Generative AI, fraudsters are now able to craft sophisticated emails that convincingly impersonate popular brands and businesses. This article delves into the growing threat of BEC attacks and explores the role of AI in facilitating social engineering-based frauds.
Perpetrators of BEC attacks use social engineering techniques to deceive victims into providing money and sensitive information, resulting in significant profits. Generative AI has played a crucial role in the success of these attacks by enabling fraudsters to create well-written emails that appear authentic and professional. The increasing prevalence of BEC attacks highlights the need for individuals and organizations to be vigilant and adopt robust security measures.
The Rise of QR Code Attacks
QR codes, once seen as convenient and trustworthy tools, are now being exploited by cybercriminals. A report by Perception Point reveals that 6% of QR codes received via email were found to be cyber attacks. This new form of fraud, known as quishing, poses a significant threat to individuals and businesses alike.
Quishing involves enticing victims to scan malicious QR codes, granting attackers access to sensitive data that can be exploited for nefarious purposes. The ease and ubiquity of QR code scanning make this type of attack particularly concerning. It is crucial for individuals to exercise caution when scanning QR codes and for businesses to implement strong security measures to protect against this emerging threat.
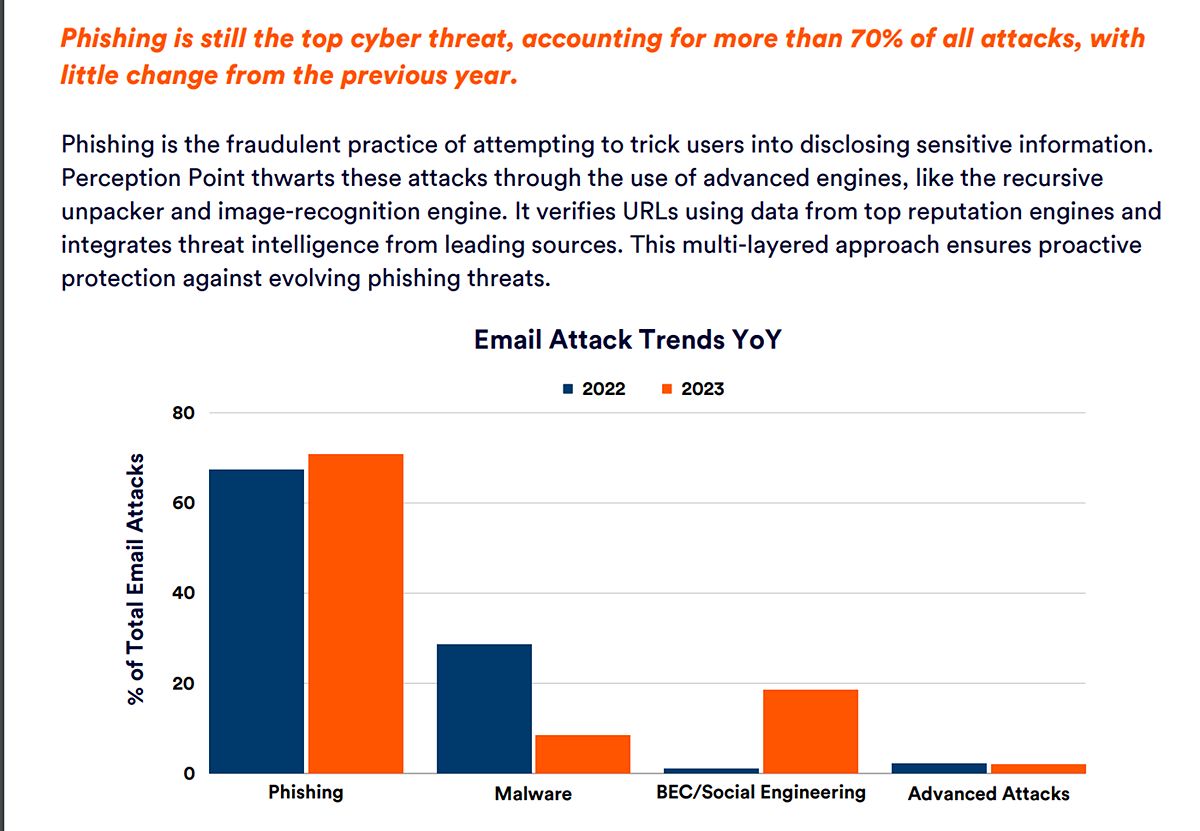
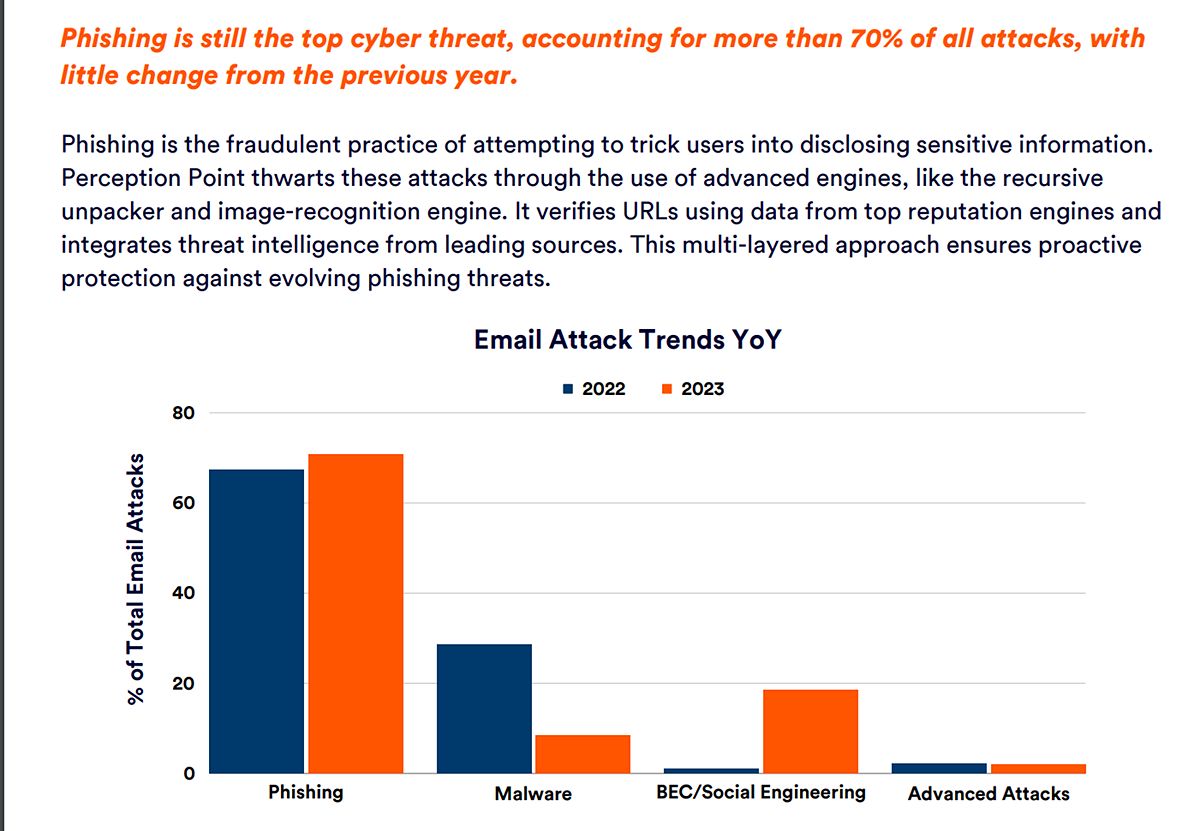
Phishing Remains the Top Cyber Security Threat
Despite the rise of BEC attacks and QR code-related frauds, phishing remains the most prevalent form of cyber attack, accounting for 70% of reported incidents. Phishing attacks rely on various methods such as email, text messages, or fake websites to trick individuals into divulging sensitive information.
These attacks exploit human vulnerabilities, relying on individuals' trust and lack of awareness. It is crucial for individuals to be cautious when interacting with emails, messages, or websites that may be phishing attempts. Education and awareness are key in combating this ongoing threat.
Two-Step Phishing Attacks: Hacking Legitimate Websites
In addition to BEC and QR code attacks, there is a rise in two-step phishing attacks where attackers compromise legitimate websites belonging to reputable companies. By doing so, they gain the trust of unsuspecting victims and exploit their interactions with these compromised platforms to extract sensitive information.
This evolving trend highlights the growing sophistication of social engineering threats. It is essential for individuals to exercise caution when interacting with websites and to verify the legitimacy of the platforms they are accessing. Companies must also prioritize cybersecurity measures to protect their websites and their customers from these types of attacks.
Conclusion
The rise of Business Email Compromise attacks and the emergence of QR code-related frauds highlight the evolving cyber threat landscape. Generative AI has enabled fraudsters to create convincing emails, while the exploitation of QR codes poses a new challenge to data security.
Phishing attacks continue to dominate the cyber threat landscape, emphasizing the need for ongoing awareness and proactive cybersecurity practices. It is crucial for individuals and organizations to remain vigilant and adopt robust security measures to mitigate the risks posed by these evolving forms of online fraud.