Learn how cybersecurity process mining can enhance your organization's cybersecurity program by leveraging data science and process management analysis. Gain valuable insights, streamline operations, and enhance compliance adherence.
Understanding the Challenge of Security Tool Sprawl
In today's rapidly evolving cybersecurity landscape, organizations face a significant challenge - tool sprawl. Managing numerous tools aimed at protecting different aspects of infrastructure can be overwhelming. These tools often lack integration and utilize different data formats, making it difficult to gain a comprehensive understanding of findings and insights. Gutsy, a leader in cybersecurity process mining, offers a solution to this problem.
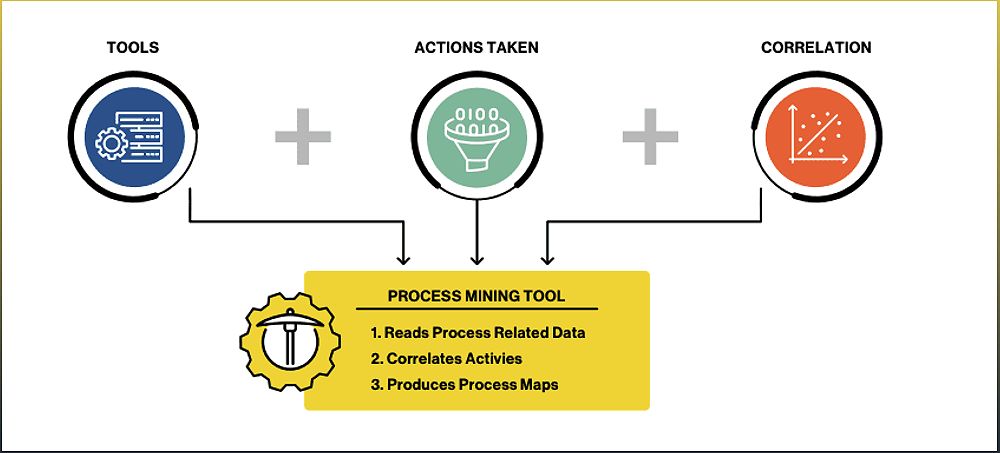
Gutsy leverages process mining to help organizations visualize and understand how their cybersecurity processes, tooling, and environments operate. By analyzing event data logs, Gutsy provides a real-time view of the organization's cybersecurity landscape. This visualization enables risk identification, reveals inefficiencies in security operations, and streamlines processes for enhanced effectiveness.
Moreover, process mining plays a crucial role in compliance, enabling organizations to adhere to regulatory requirements and minimize organizational risks. With Gutsy's expertise in cybersecurity process mining, organizations can overcome the challenges posed by security tool sprawl and achieve a more effective cybersecurity program.
The Importance of People, Process, and Technology in Cybersecurity
Cybersecurity is not solely a technological problem. Experienced security professionals understand the importance of people, process, and technology in securing an organization. While advanced technologies and tools are essential, without well-documented processes and a competent workforce, optimal security outcomes cannot be achieved.
Gutsy recognizes this paradigm and applies process mining to cybersecurity. By analyzing data flows and interactions, Gutsy helps organizations identify core problems, streamline operations, and enhance compliance adherence. This holistic approach empowers organizations to address cybersecurity challenges effectively.
Unlocking the Potential with Cybersecurity Process Mining
Gutsy's application of process mining to cybersecurity unlocks significant potential for organizations. By leveraging data science and process management analysis, organizations can gain a comprehensive view of their cybersecurity processes, tooling, and environments. This enables risk identification, streamlines operations, and enhances compliance adherence.
Cybersecurity process mining also provides data-driven insights and transparency. It goes beyond guesswork and offers valuable insights into the effectiveness of cybersecurity tools and investments. This empowers organizations to make informed decisions about additional investments or rationalizing their tooling portfolio.
Embracing cybersecurity process mining is crucial for organizations and security leaders to stay ahead in an ever-changing threat landscape. By adopting this innovative approach, organizations can revolutionize their cybersecurity programs and enhance their overall security posture.
Conclusion: Unleash the Power of Cybersecurity Process Mining
Cybersecurity process mining represents a significant step forward in the evolution of cybersecurity. By leveraging data science and process management analysis, organizations can gain a holistic view of their cybersecurity processes, tooling, and environments. This enables risk identification, streamlines operations, and enhances compliance adherence.
As the industry continues to demand data-driven insights and transparency, embracing cybersecurity process mining will become a crucial element in an organization's cybersecurity strategy. The time has come for organizations to unlock the power of process mining and revolutionize their cybersecurity programs.